3 Vulnerabilities In Zoom Allow Hackers To Intercept Data From Meetings

3 Vulnerabilities In Zoom Allow Hackers To Intercept Data From Meetings The vulnerability resides in zoom on permise meeting connnector controller and has been updated for version 4.6.358.20210205. finally, experts found that cve 2021 34416 could facilitate some risk scenarios by injecting certain commands. Zoom workplace apps for ios improperly sequence security checks, enabling attackers to intercept authentication tokens or meeting metadata before validation completes. this vulnerability could expose enterprise level data in hybrid work environments.
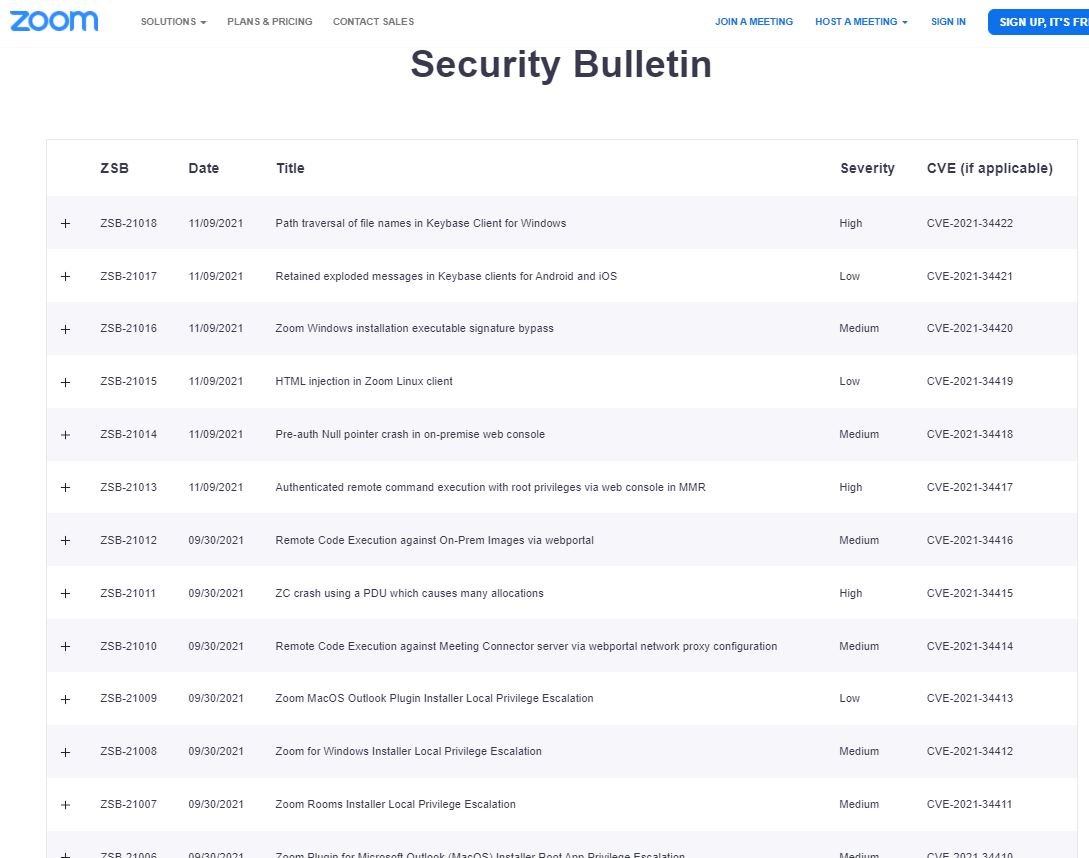
3 Vulnerabilities In Zoom Allow Hackers To Intercept Data From Meetings Exploiting this zoom vulnerability allows attackers to hijack meetings, manipulate the contacts feature, infiltrate organization wide whiteboards, and extract sensitive data from team chat channels, even without an invitation. A critical vulnerability, cve 2025 0147, was discovered in the zoom workplace app for linux (versions prior to 6.2.10). this type confusion vulnerability could allow an attacker to escalate privileges via network access. Zoom’s offensive security team discovered and addressed several critical vulnerabilities, including cve 2025 27440, cve 2025 27439, cve 2025 0151, and cve 2025 0150, demonstrating the company’s proactive approach to securing its platform. Cybersecurity researchers have helped patch three vulnerabilities in zoom that could have allowed criminals to intercept data from meetings and attack customer infrastructure.

Protect Your Zoom Meetings From Hackers Boomtech It Inc Zoom’s offensive security team discovered and addressed several critical vulnerabilities, including cve 2025 27440, cve 2025 27439, cve 2025 0151, and cve 2025 0150, demonstrating the company’s proactive approach to securing its platform. Cybersecurity researchers have helped patch three vulnerabilities in zoom that could have allowed criminals to intercept data from meetings and attack customer infrastructure. The vulnerabilities primarily impact zoom workplace, zoom rooms controller, zoom rooms client, and zoom meeting sdk versions prior to 6.3.0. attackers exploit these flaws through memory related issues and improper data verification, enabling unauthorized access and system crashes. Check point found that the vulnerabilities, which have been patched by zoom since their disclosure last year, would enable a hacker to eavesdrop into zoom meetings by generating zoom meeting ids,. Zoom says it uses aes 256 encryption to encrypt video and audio data traveling between zoom servers and zoom clients (ie you and me). but researchers at the university of toronto’s citizen lab found in an april 3 report that zoom actually uses the somewhat weaker aes 128 algorithm. This vulnerability existed in zoom rooms, a system developed by zoom to allow team members from different locations to work together over zoom. a threat actor could potentially exploit this vulnerability and gain access to the victim organization’s tenant.

163 Zoom Meetings And Hackers Stock Photos High Res Pictures And The vulnerabilities primarily impact zoom workplace, zoom rooms controller, zoom rooms client, and zoom meeting sdk versions prior to 6.3.0. attackers exploit these flaws through memory related issues and improper data verification, enabling unauthorized access and system crashes. Check point found that the vulnerabilities, which have been patched by zoom since their disclosure last year, would enable a hacker to eavesdrop into zoom meetings by generating zoom meeting ids,. Zoom says it uses aes 256 encryption to encrypt video and audio data traveling between zoom servers and zoom clients (ie you and me). but researchers at the university of toronto’s citizen lab found in an april 3 report that zoom actually uses the somewhat weaker aes 128 algorithm. This vulnerability existed in zoom rooms, a system developed by zoom to allow team members from different locations to work together over zoom. a threat actor could potentially exploit this vulnerability and gain access to the victim organization’s tenant.

Zoom Vulnerabilities Allow Attackers To Escalate Privileges Zoom says it uses aes 256 encryption to encrypt video and audio data traveling between zoom servers and zoom clients (ie you and me). but researchers at the university of toronto’s citizen lab found in an april 3 report that zoom actually uses the somewhat weaker aes 128 algorithm. This vulnerability existed in zoom rooms, a system developed by zoom to allow team members from different locations to work together over zoom. a threat actor could potentially exploit this vulnerability and gain access to the victim organization’s tenant.

Comments are closed.